An effective government backstop would require preexisting consensus on security standards, data sharing, and cooperation.

The scale of the July 19 CrowdStrike outage was a stark reminder of the global connectivity and systemic nature of the digital economy. The outage affected most industries and continues to cause concern, especially among insurers who worry about systemic risk and the ability of the market to absorb the potential quantum of loss in a significant cyber incident.
Several prominent insurers have expressed skepticism about the insurability of cyber risk and have argued that only a government backstop will bring confidence to more broadly insure cyber risk. Recently, a leading insurance broker and a global insurer, Marsh McLennan and Zurich, released a joint report stressing the urgent need for such public-private partnership solutions.
Such recommendations should be viewed with caution: A federal backstop is not a silver bullet. A well-structured backstop can be useful where the private insurance market will not currently participate but only when a clear demarcation between constituent markets is established, and not as a mechanism for insurers to offload complex risks onto taxpayers. A heavy-handed approach could be counterproductive by stifling innovation, disincentivizing data sharing, and reducing the pressure on businesses and insurers to require adherence to the most foundational cybersecurity practices. Before a backstop can be finalized, cybersecurity and insurance professionals must engage in more collaboration, identifying and sharing claims, trends, and systemic risk data that will enable better traditional management of the risk (prevention, mitigation, and transfer with appropriate feedback loops). The 2024 World Economic Forum reminds us that risk resilience begins with insurers stepping confidently: “Historically, insurance has been the de facto security moderator in every risk stack, taking on most of the burden of standardizing risk mitigation technology and processes across industries.”
It is important to identify the industries that need to collaborate and data that needs to be shared to efficiently and continuously build resilience and transfer residual risks to a confident private insurance sector where knowledge and data replace fear. This approach has allowed the private sector to greatly improve resilience to most risks in the economy—cyber is no different.
From Zero to AI in 30 Years: Cars Without Breaks
Digital activity has replaced physical assets as the primary engine of economic growth and market capitalization virtually overnight. Incredibly profitable opportunities have emerged from this transformation, with innovation as the main, and sometimes only, focus. Successful businesses launched seemingly overnight with laptops and internet connections, emails replaced paper, and data centers replaced warehouses—but security and risk management were often an afterthought, if not a distraction from innovation.
The U.K. National Cyber Security Centre has underlined this behavior as businesses race toward the deployment of artificial intelligence (AI)-enabled solutions: “AI systems are subject to novel security vulnerabilities that need to be considered alongside standard cyber security threats. When the pace of development is high—as is the case with AI—security can often be a secondary consideration.” When security is not embedded in risky activities, outcomes can be disastrous, like building and selling sports cars without brakes or airbags.
Most large corporations have realized this over the past decade and invested heavily in cybersecurity, which they have now priced into their services as a cost of doing business. The public sector and small and medium-sized enterprises, by contrast, are far behind. Operating a digital business requires similar risk management methods (policy compliance, governance, security, and adequate insurance) to what is standard or best practice in the tangible world. However, cyber risk management is usually primitive. Cybersecurity is too often self-managed by businesses that are not equipped to face dynamic threats and fast changing technology. Cyber risk assessment methods are usually based on estimated aggregated market and incomplete risk data and emerging risk analytics, rather than using comprehensive, granular, and verifiable data that feeds modern exposure-based analytics tools. Risk transfer products (insurance) are limited in breadth and depth and poorly understood—with various limitations and exclusions—by all stakeholders. Last but not least, the cyber (re)insurance industry has a limited grasp on systemic risk.
As the digital age has dawned, so too have related industries, including cyber risk management, cybersecurity, or cyber insurance. Cyber insurance is experiencing the fastest premium revenue growth across all insurance lines, as Figure 1 shows, highlighting the need for adequate risk data to support the professional risk management of increasing insurer liabilities.
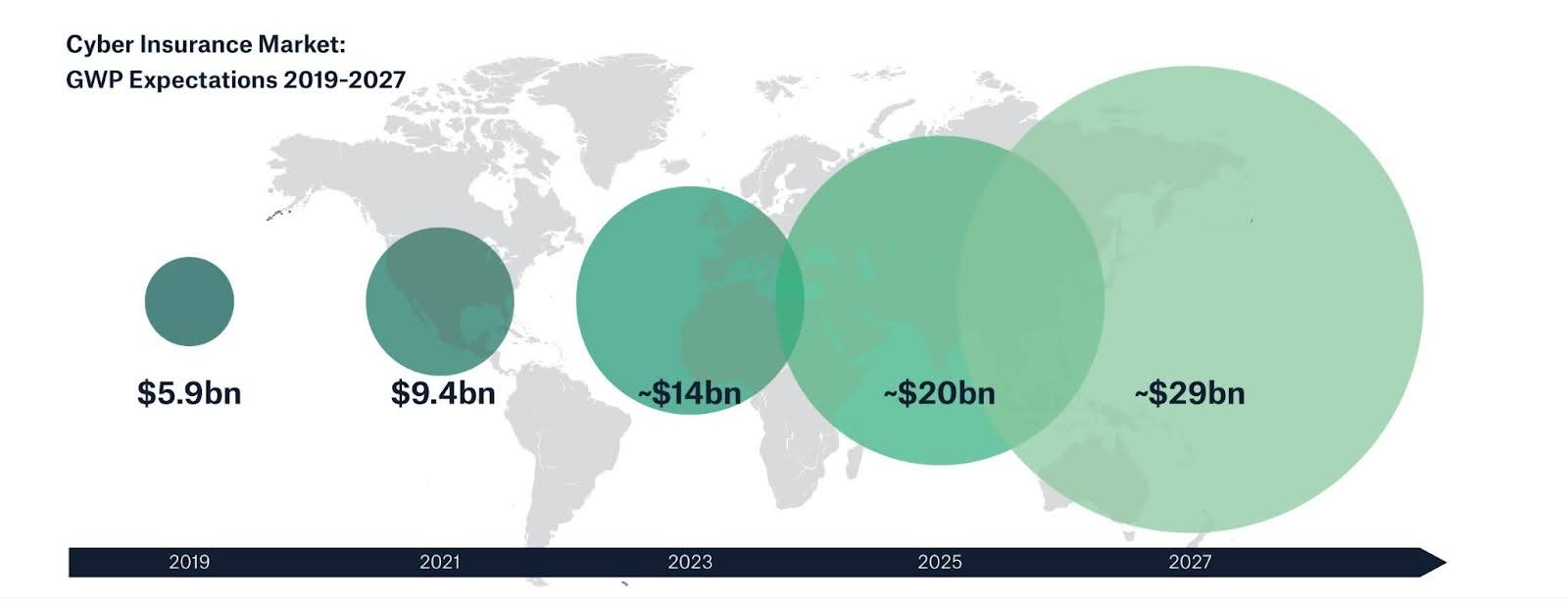
The lack of security standards and wide diversity of views in critical areas (security, risk assessments, insurance coverage, and systemic risk understanding) result in divergent risk views and poor visibility of potential systemic cyber incident consequences. Absent credible risk data, fear takes the front seat.
Consequently, insurance executives have questioned the ability of insurance market capital to absorb a remote but possible cyber-systemic event, calling for a government-sponsored financial backstop to ensure insurers can continue to provide coverage for risks potentially too large for the private sector to manage. Such a backstop typically specifies purpose, definition of events covered (or excluded), its limits, geographic boundaries, premium and liability sharing with insurers, conditions for federal payments, whether and when participation is mandatory for insurers, administration of claims, etc.
But jumping to conclusions of un-insurability without a better understanding of the risk, through data, is premature. In other words, calls for a government backstop should be combined with demand for cooperation among security vendors, security service providers, insurers, and regulators to better understand the risk and private-sector solutions.
Learning From Existing Backstops
The backstop solution recommended by insurers is similar to the 2002 Terror Risk Insurance Act (TRIA) established to provide a government backstop to a (then) emerging risk, which was—similar to cyber—poorly understood and posed potentially disastrous consequences to insurers. Under the TRIA, insurers share with the government the burden of a monetary loss from a terrorism event and, as a result, do not exclude all terror coverage in their policies.
Studying TRIA and other systemic risk government-backed financing, including lessons from both the public and private sectors, offers guidance around structuring a successful backstop. Other examples are hurricane insurance wind pools across all Gulf states, Florida, and the Eastern Seaboard, or the National Flood Insurance Program, to name a few. While these have enjoyed some successes, they also face the ongoing challenge of providing subsidized insurance while not stifling insureds’ risk prevention, security, and mitigation measures and disincentivizing private insurance sector innovation, competition, and capital deployment.
The evolution of natural disaster insurance over the past 30 years presents a good analogy to the cyber insurance state today and where it should go if it follows a similar maturation. Significant storms, hurricanes, and earthquakes occurred around 1990 in Europe and the U.S., causing losses large enough to bankrupt several insurance companies. Others soon left the natural catastrophe insurance market, prompting various backstops to be structured to provide the critical insurance needed to protect property at risk.
The backstops mentioned above were specific—not overly large or broad—and did not disincentivize private market solutions across innovation, data collection and sharing, and cooperation. They also enabled a new private risk capital solutions market, worth in excess of $100 billion today, in addition to a competitive traditional (re)insurance market.
The property insurance market for natural disasters saw profound transformation through risk data collection, risk modeling, preventive designs, and building codes enforcement to reduce vulnerabilities, resulting in existing and new risk takers (re)entering, with renewed confidence, a market that no longer questions its insurability. Figure 2 shows how data granularity enables the insurance market to mature and attract investors. It illustrates how little insurers used to know about hurricane risk exposure. The cyber risk management industry today is virtually identical to the state of the hurricane insurance market in the 1980s.
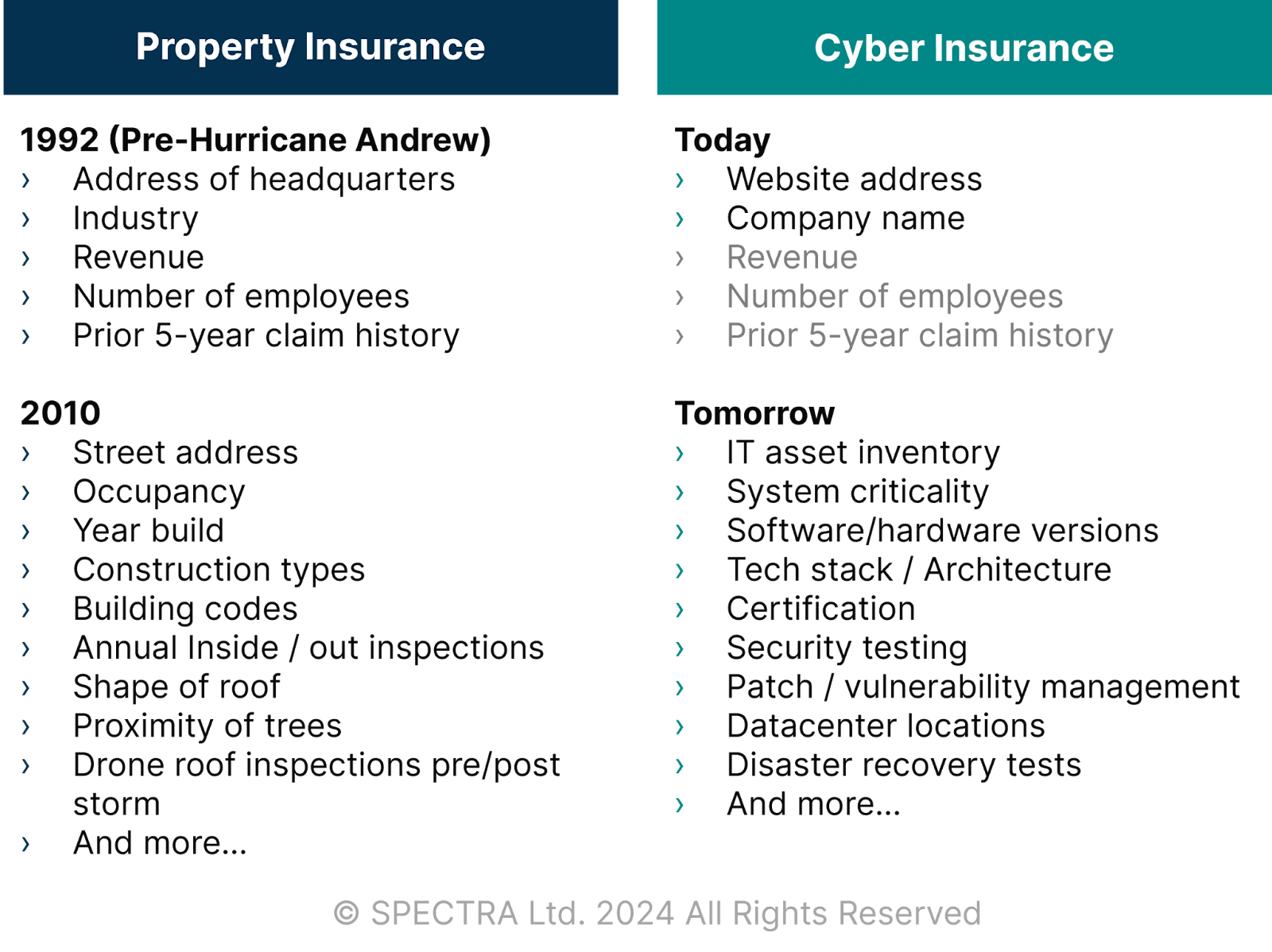
The reason insurers and some elected officials are so focused on government backstopping extreme cyber event losses is the lack of confidence in cyber risk analytics and modeling, in particular around systemic risk scenarios (e.g., a public cloud or CrowdStrike-like supply chain outage, cyber war, infrastructure failure). The lack of confidence has two origins.
First and foremost, lack of retrospection and the short (20-year) history of cyber insurance make it challenging to infer what a remote but plausible systemic cyber event would cost. (Insurers use probable maximum loss metrics, with, usually, a 0.4 percent probability of an event occurring, to manage their catastrophic risk appetite—this would be the most costly event the insurer can expect to see through a 250-year period.)
The second reason is that the cyber insurance industry does not access technographic data about their policyholders. In other words, insurers do not know what technology is deployed, the location of the data center(s), or what resilience has been implemented (disaster recovery solutions, data replication, tech diverse resilient solutions, etc.). This lack of visibility does not allow insurers to confidently account for (and reward) built-in resilience, and the worst-case scenario often assumes no resilience.
Simply knowing the company domains and industry verticals offers very limited information regarding internal controls and technology deployed inside the network and the potential impact of a cyber incident. Insurers for large companies rely on “yes/no” questionnaires that often lack context and specifics and, more important, cannot be relied on as they are never verified.
Risk inspection is a standard process in all insurance lines of business except for cyber insurance, where the insurers and the brokers do not have access to the network covered by the policy. This inability to inspect results in insufficient access to risk data and a poor understanding of the policyholder risk. Good security posture does not get the credit it deserves and often subsidizes other policyholders with less risk posture. Using the hurricane analogy above, the insured in Wisconsin pays the same hurricane insurance premium as the policyholder in Florida.
Why Cybersecurity Data Is Key for Insurers
The implementation of a well-designed cyber backstop should be paired with a cross-industry program focusing on cooperation, relevant risk data sharing, establishment of cybersecurity code and its enforcement, and subventions to accelerate adoption in the public sector. This will significantly develop the (re)insurance market’s appetite for cyber risk and ultimately provide a more diversified resilience to cyber threats.
Regarding granular technographic data collection, it is also critical to understand not just what technologies are used but also how controls are managed. Insurers need to inspect and collect evidence of technology and processes deployed to secure the digital environment of their policyholders (see Figure 2, above). The lack of cybersecurity standards means that insurers and cybersecurity vendors and providers need to cooperate and establish foundational security standards and allow for regular (annual) inspections. The controls are particularly important; most businesses, for example, do not have the resources to provide expertise continuously (24/7/365) across fast-changing technology and evolving threats. Leading cyber insurers are seeing this through the claims data and forensics work of cyber incidents: Poorly configured identity and access management controls, untested backups, and unmanaged endpoint security solutions are some of the most common sources of increased claim activity in recent years.
Security standards, technographics, and control data sharing will enable insurers to better understand resilience (or lack thereof) and accumulation of risk across technology (cloud infrastructure, data center, etc.) but also supply chain risk (i.e., the CrowdStrike outage).
Similarly, insurers should communicate loss trends, that is, the types of incidents leading to severe claims, with security vendors and providers so that the security market can improve technology and controls to mitigate risks leading to such claims. Also, insurers, having access to better risk data (from security vendors and providers), will be able to map systemic risk more precisely, resulting in much more adequate pricing that reflects the built-in resilience of certain security solutions. This more mature understanding of systemic risk, which exists in other insurance lines of business, will help insurers to confidently deploy capital and take such risk on their balance sheets, limiting the breadth and size of a backstop.
Managed Service Providers: A Key Participant
The $250 billion U.S. market of managed service providers and managed security service providers includes 40,000 information technology and security service companies that manage technology and security for millions of business customers. They have access to the granular cybersecurity posture data and are willing to share it, but despite their alignment with insurers in protecting their customers, the two have not interacted, let alone cooperated.
Managed security data will enable risk managers to better and more granularly understand technology aggregation and resilience, which will help at regular intervals to strategically refine government backstop structure, size, and coverage and focus where the financing is most needed as insurers become comfortable taking on more risk. In summary, a more resilient and mature digital economy will come from improved cybersecurity standards setting that requires collaboration among technologists, regulators, and insurers; implementation and professional management of foundational security controls; and sharing of security posture and insurance claims trends data to improve performance. Cooperation among security software vendors, providers of managed security solutions, and insurers is critical to continuously improve resilience through feedback loops between security and cost of cyber claims, and mapping, modeling, and management of systemic risk.
Improved cybersecurity standards: Foundational security is an evolving security standards framework that reflects current and dynamic threats and is often identified by cyber insurers’ claims data. Well designed and regularly tested data security and recovery tools, endpoint protection solutions, and identity and access management controls (including multi-factor authentication) for business email and privileged accounts are regularly listed by insurers as the three solutions that would reduce cyber claims frequency by 80-90 percent.
Implementation and professional management of foundational security controls: Managed security is delivered by experienced information technology and security professionals who are equipped with the latest, tested, and properly configured technology, and it is available 24/7/365.
Sharing of security posture and insurance claims: Security posture data would evidence good design, proper implementation, and ongoing management of foundational security solutions, allowing insurance to (a) give credit to good security posture at the policyholder level, (b) recognize resilience in their systemic risk modeling, and (c) incentivize development and implementation of more resilient solutions to further reduce systemic risk. Claims data (or related trends) would inform and help security software vendors and managers of security prioritize where improvements are most urgent and impactful.
More specifically, such cooperation will allow the resilience chain to refine the understanding of extreme cyber incidents and their impact, which will (a) allow insurers to disaggregate systemic risk where appropriate—for example, if critical data is recoverable from several, isolated environments leveraging multiple cloud service providers, it is unlikely that the data will be entirely lost in a catastrophic event impacting a single provider or environment; (b) apply risk reduction, technology (vendor) diversification, and other resilience solutions strategically within the portfolio; and (c) price adequately and transfer residual systemic risk to reinsurers and capital market investors. As this virtuous cycle continues, the backstop solution becomes more strategic and clearly defined.
Policymakers have an opportunity to engage with key stakeholders who will enable the collaboration needed in the market. Partnerships among vetted managed service providers, tech and security software vendors, and cyber systemic risk experts (such as reinsurers and insurance brokers)will clarify the current systemic cyber market appetite, where these actors do not want to engage and why, and what could progressively help them develop broader appetite for cyber and systemic risk—reducing the need for a backstop.
***
As connected devices continue to come online at an accelerated rate, and as we continue deploying new transformative digital solutions such as AI, the collective attack surface that malicious actors can exploit will only grow exponentially. Likewise, the potential impact of non-malicious outages grows just as fast with consolidation of leading vendors. For cyber resilience to be developed, monitored, and controlled, a combination of solutions must be deployed in addition to government support, including the establishment of foundational cybersecurity best practices, cooperation through data, and knowledge sharing across vendors, providers, and insurers. Without these prerequisites, federal backstops are likely to worsen the issues, not solve them. Indeed, Marie Curie summarizes the situation well: “Now is the time to understand more, so that we may fear less.”
– Edouard von Herberstein is founder and CEO of Spectra, a cyber insurance company in Bermuda that partners with cybersecurity and re-insurer partners. He was a founding team member of ILS Fund Hudson Structured Capital Management (HSCM). Published courtesy of Lawfare.


