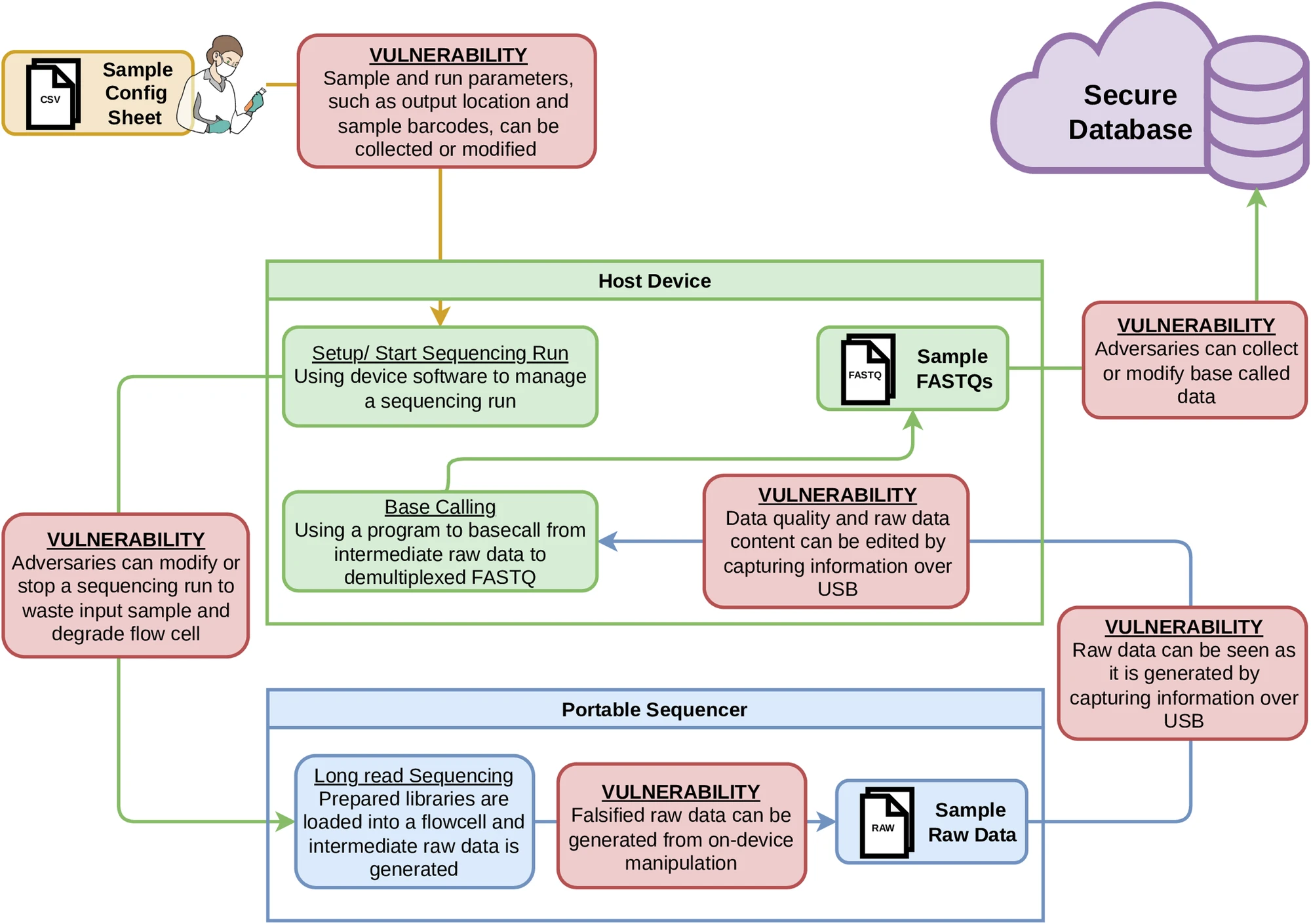
Portable genetic sequencers used around the world to sequence DNA have critical, previously unreported security…
STRATEGY & THREATS
Ukraine’s offensive cyber strategy demonstrates that Western governments need to adopt a “responsibly irresponsible” warfighting…
Persistent penetration of domestic networks makes coordinated defenses and robust deterrence essential to preventing cyber…
A major Japanese beverage producer says it has been hit by a cyberattack that left…
Authoritarian threats, coupled with ongoing corporate surveillance, demand that we rethink how we use digital…
Restricting untrusted components from Europe’s subsea data cables strengthens governments’ national security and benefits European…
Precisely targeted cyber operations can remove blocking rules or disable network-blocking equipment. Cyberspace and the…
Vibe coding produces software riddled with insecurities. Will risk management and regulatory compliance, too, fall…
Criminals can use artificial intelligence, specifically large language models, to autonomously carry out ransomware attacks…
Cyber contingency campaigning, involving sustained cyber activity in peacetime, could be strategically impactful in a…



.jpeg?sfvrsn=f8ab7a0d_5)


.jpeg?sfvrsn=d5075110_5)



