Grok’s nudification scandal shows how “free speech” rhetoric is being used to obscure any ethical…
STRATEGY & THREATS
With $800 of off-the-shelf equipment and months worth of patience, a team of U.S. computer…
Unilateral controls leave allies to fend for themselves. Collective resilience is in all of their…
An evaluation of AI policy recommendations by Anthropic’s CEO may help guide ongoing regulatory efforts…
The U.K. government’s latest attempt to access encrypted cloud backups could allow adversarial actors to…
On Dec. 3, the White House backed away from sanctioning China’s spy agency, the Ministry of State…
The country’s anticipated cyber strategy will need to sharpen its focus while better implementing its…
A review of Eliezer Yudkowsky and Nate Soares, “If Anyone Builds It, Everyone Dies: Why…
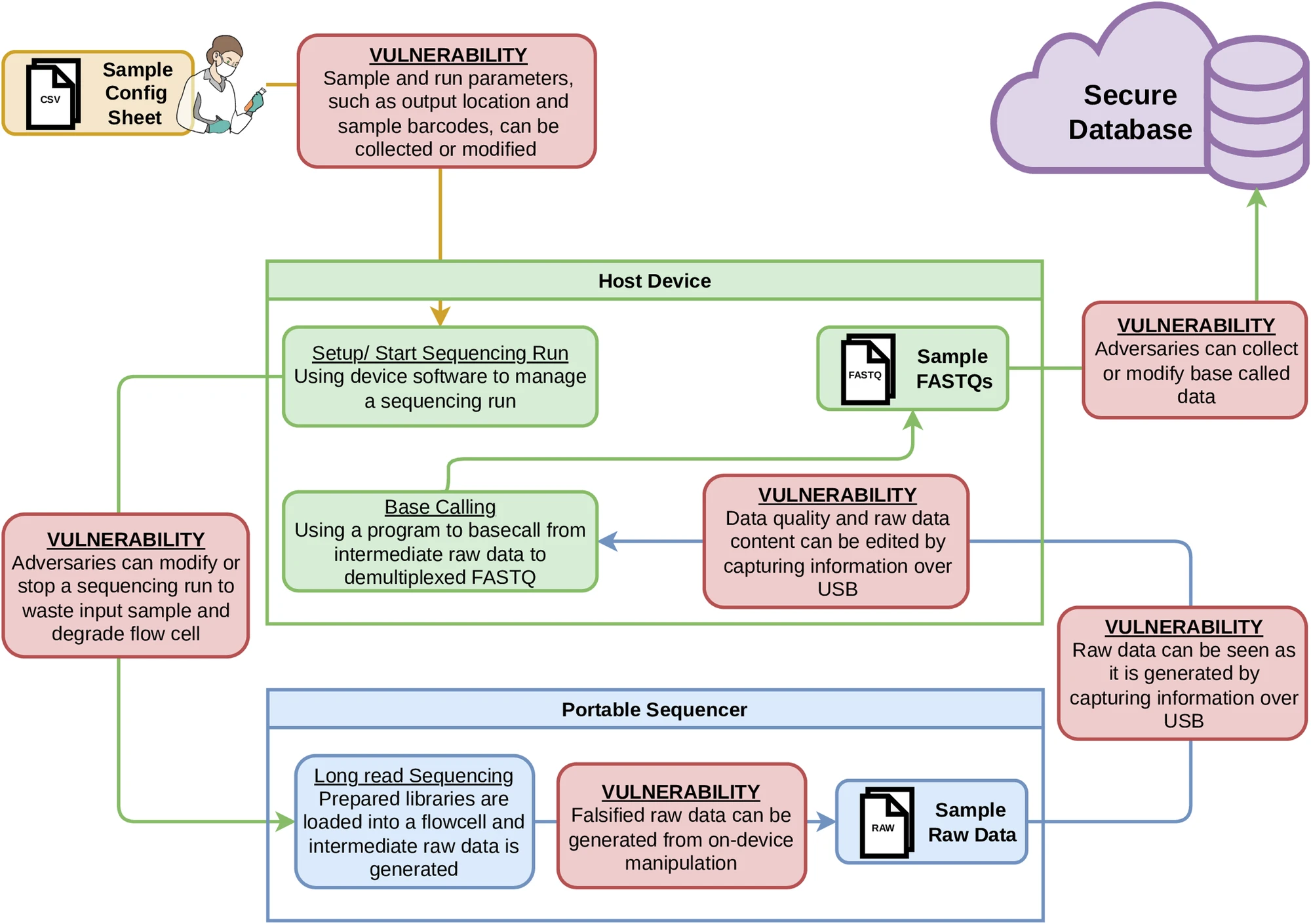
Portable genetic sequencers used around the world to sequence DNA have critical, previously unreported security…
Ukraine’s offensive cyber strategy demonstrates that Western governments need to adopt a “responsibly irresponsible” warfighting…




.jpg?sfvrsn=c5a4ff6d_5)