If Society Wants to Slow Down the Rollout of This Potentially Epochal Technology, It Will Have to Do It the Old-Fashioned Way: Through Top-Down Government Regulation. It was a wild week at…


If Society Wants to Slow Down the Rollout of This Potentially Epochal Technology, It Will Have to Do It the Old-Fashioned Way: Through Top-Down Government Regulation. It was a wild week at…

With FISA Section 702 soon set to expire, two Senate bills and a House report frame the reauthorization debate as it comes down to the wire. The clock is ticking on reauthorization…

Ransomware criminals continue to make hay despite increased government efforts worldwide to clamp down on the ecosystem. What’s next? Last week, the U.S. financial services division of China’s biggest bank, the state-owned…

The National Cybersecurity Strategy calls for new and harmonized cyber regulations. To succeed, there is a lot of homework left to do, starting with a better understanding of performance-based and other kinds…

The Howard Hughes Medical Institute (HHMI) awarded Rice University with $2.5 million spanning over five years as part of its Driving Change initiative designed to connect research universities that are working to build inclusive…
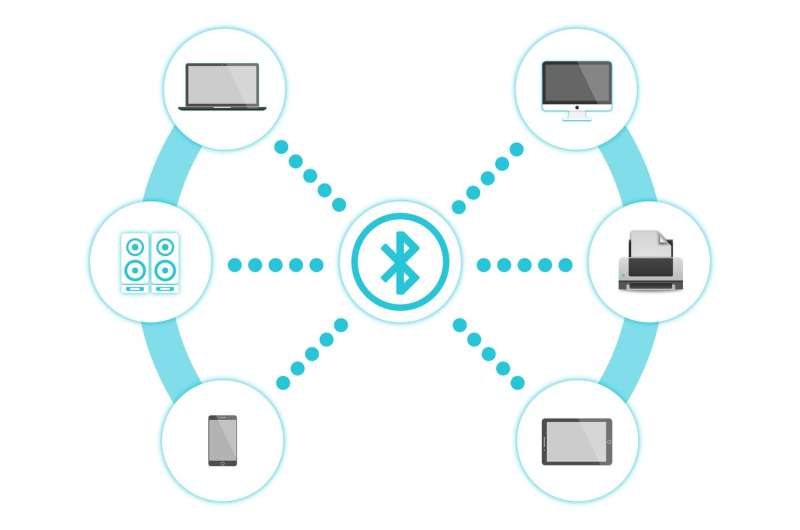
University of Sussex researchers have developed a more energy-efficient alternative to transmit data that could potentially replace Bluetooth in mobile phones and other tech devices. With more and more of us owning…
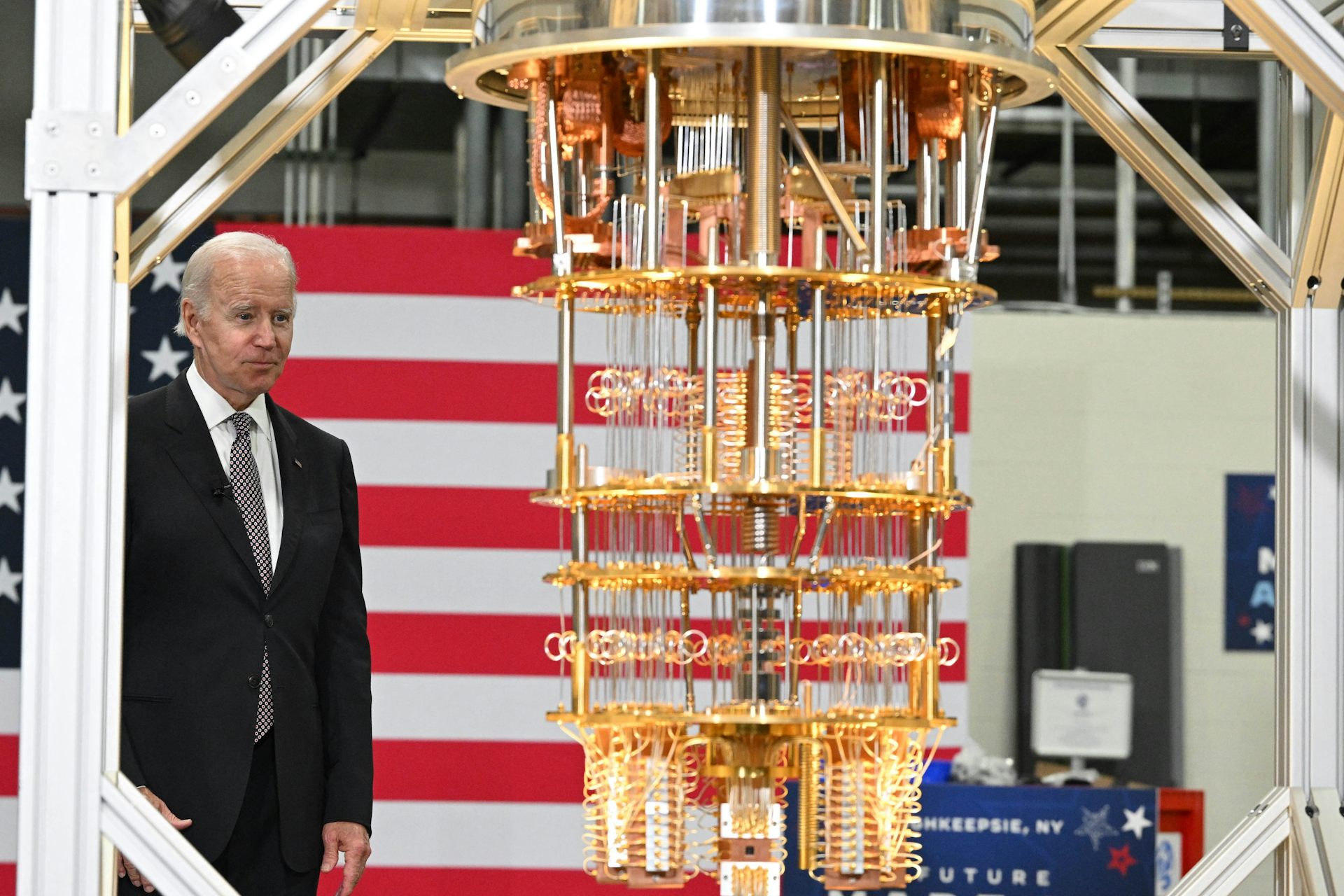
Quantum advantage is the milestone the field of quantum computing is fervently working toward, where a quantum computer can solve problems that are beyond the reach of the most powerful non-quantum, or…

Ransomware criminals continue to make hay despite increased government efforts worldwide to clamp down on the ecosystem. What’s next? Last week, the U.S. financial services division of China’s biggest bank, the state-owned…

Law enforcement has been buying sensitive personal data for use in investigations, but these purchases likely violate the Fourth Amendment. The United States lacks a comprehensive data privacy statute, and most states…