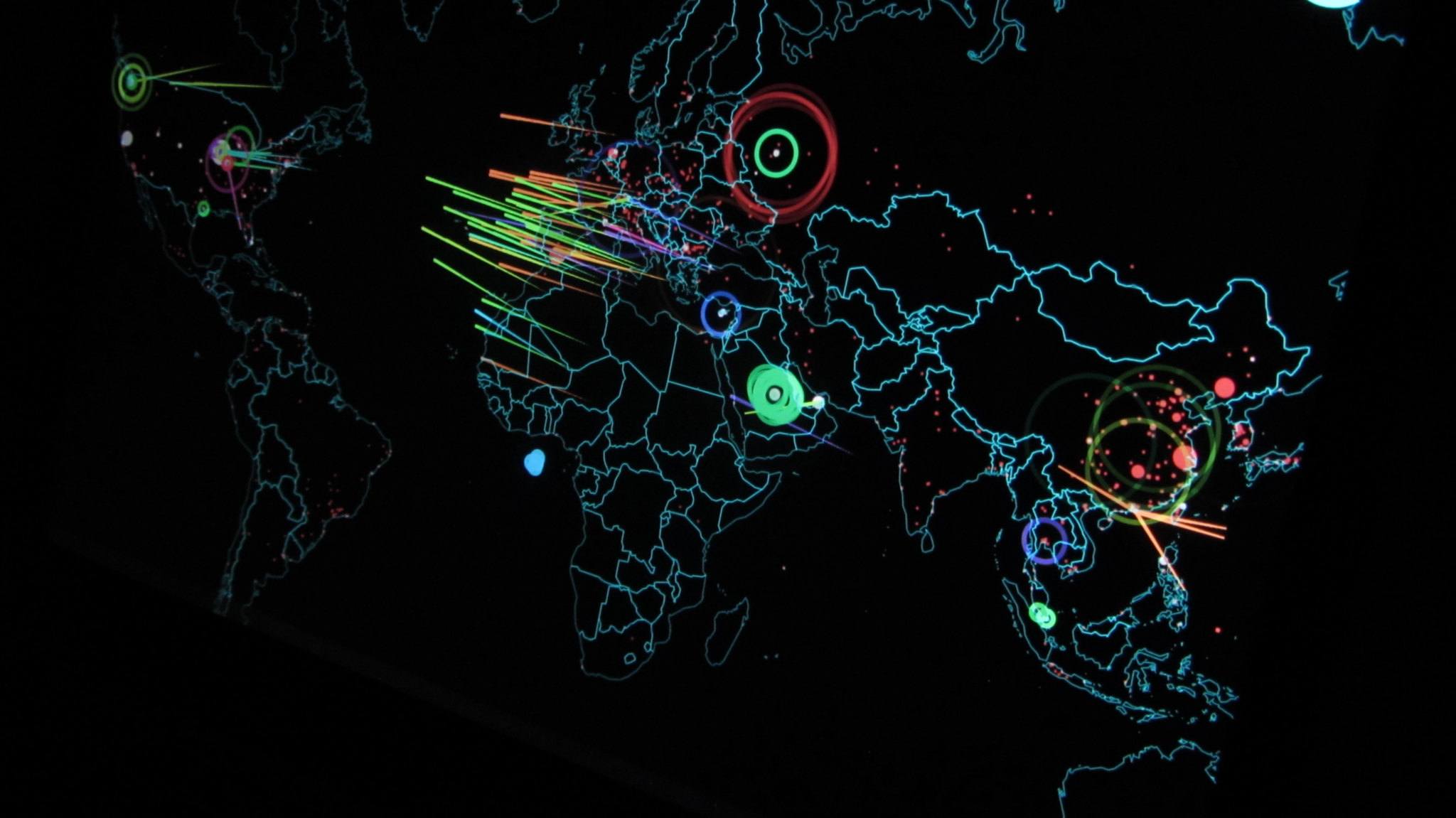
Can regulators know when autonomous weapons systems are being used? Editor’s Note: For those eager to…
STRATEGY & THREATS
On Monday, editor-in-chief of The Atlantic Jeffrey Goldberg revealed that he had apparently been added…
Security was top of mind when Dr. Marcus Botacin, assistant professor in the Department of…
Sophos’s account of its recent active cyber defense campaign can help shape norms of “responsible…
In the ever-evolving landscape of wireless communication, security remains a paramount concern. A recent study…
Challenge Provides Industry Partners Unique Opportunity to Test, Refine and Showcase Remote Identity Technologies The…
CrowdStrike has released its 2025 Global Threat Report, exposing the growing aggression of China’s cyber…
Musk and his DOGE associates’ reported access to sensitive government systems presents serious cybersecurity risks.…
The international community needs a new model for maintaining peace and security in cyberspace. The…
Cybercrime is on the rise. International hubs will solve the problem. Editor’s Note: Cybercrime, already high,…