Shortly after 4 a.m. on a crisp, cloudless September morning in 1859, the sky above…
STRATEGY & THREATS
On March 23, the US Department of Justice commenced perhaps the largest prosecution of a…
Computer users — at home and at work — often engage in behaviors that create…
A new study by researchers Nikolaos Gatsis, David Akopian and Ahmad F. Taha and their…
Security vulnerabilities in technology extend well beyond problems with software. Earlier this month, researchers revealed…
The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has awarded 418 Intelligence Corporation…
Software developers are working to release fixes and updates to protect computers and mobile devices…
It’s 7am and I’m driving down Hull city centre to pick up Brett Johnson, known…
Many Americans don’t feel they personally are at risk of a cyber attack. However, a…
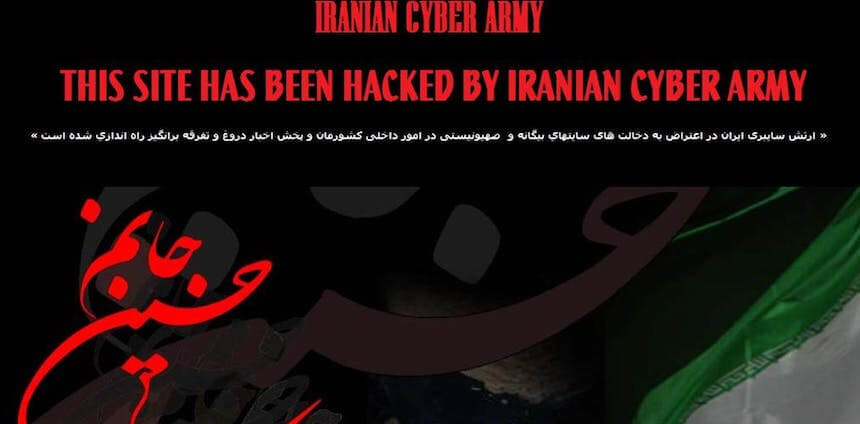
Iran is one of the leading cyberspace adversaries of the United States. It emerged as…