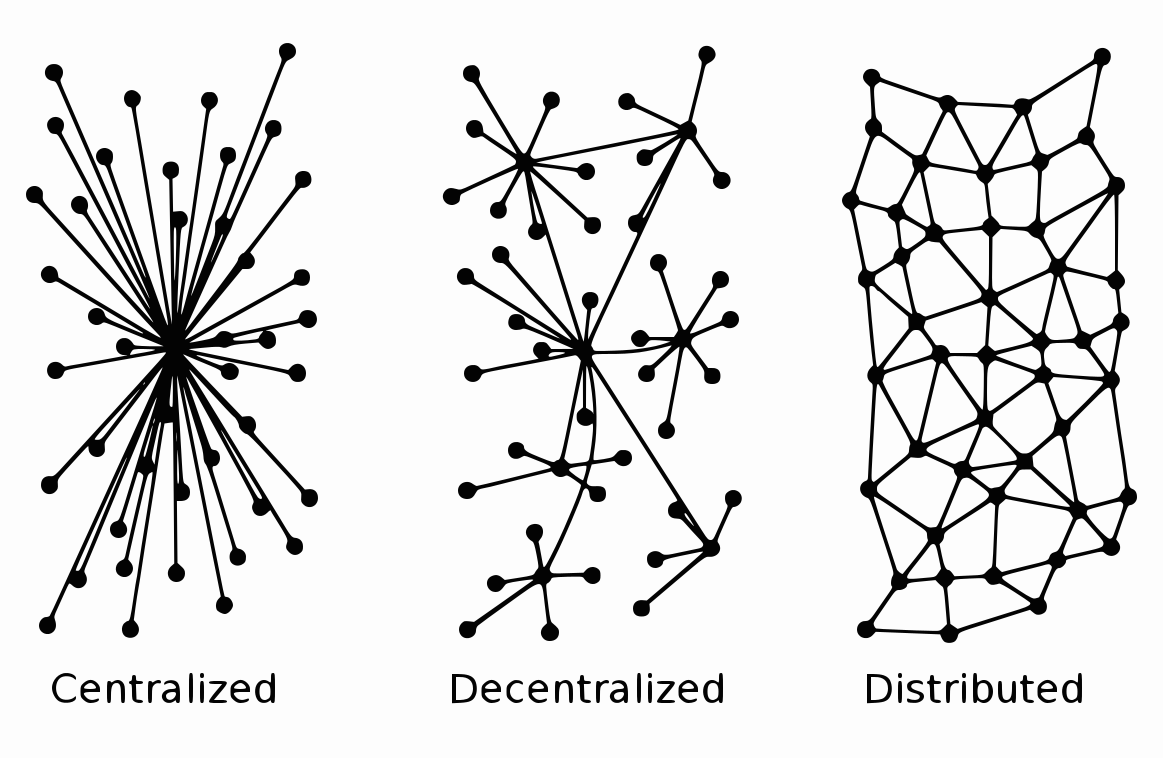
President Joe Biden’s cybersecurity executive order, signed May 12, 2021, calls for the federal government…
STRATEGY & THREATS
Takeaways: · There are no easy solutions to shoring up U.S. national cyber defenses. ·…
Having your social media account hacked is a pain. Having your credit card account hacked can…
From power grids and telecommunications to water supply and financial systems, digital data controls the…
Researchers have found a way to use chaos to help develop digital fingerprints for electronic…
Billions of people’s lives changed across the world when the pandemic began, as we experienced…
A Delphi survey carried out by Dr. Lyn Robinson, Head of Department and Reader in…
University at Buffalo computer scientists have developed a tool that automatically identifies deepfake photos by…
In the past five years, ransomware attacks have evolved from rare misfortunes into common and…
A total of 1.1 million bitcoin were stolen in the 2013-2017 period. Given the current…