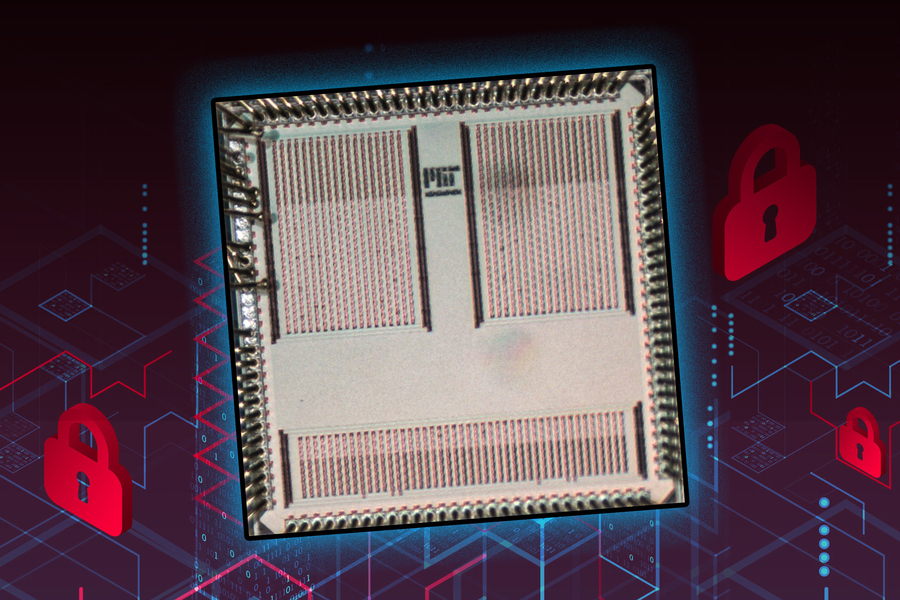
Engineering researchers have developed a new approach for implementing ransomware detection techniques, allowing them to…
STRATEGY & THREATS
When the draft of a Supreme Court decision that would overturn Roe v. Wade was…
A new form of security identification could soon see the light of day and help…
Sociologists at the Ural Federal University (UrFU) have identified digital fears among young people. According…
Federal officials have warned U.S. financial institutions to prepare for the possibility of Russia-linked cyberattacks…
On March 21, President Biden issued an urgent warning to American business leaders to strengthen their companies’…
Born in eastern Ukraine and raised in the city of Artemovsk (recently renamed Bakhmut), Cal…
The frequency and severity of cyber attacks on critical infrastructure is a subject of concern…
Multiple programs running on the same computer may not be able to directly access each…
A heart attack patient, recently discharged from the hospital, is using a smartwatch to help…