Faculty members at Binghamton University, State University of New York have received two grants to study whether 5G can be used similarly to radar by creating images based on how the carrier…


Faculty members at Binghamton University, State University of New York have received two grants to study whether 5G can be used similarly to radar by creating images based on how the carrier…

The Center for Applied Internet Data Analysis, or CAIDA, at the San Diego Supercomputer Center (SDSC) at UC San Diego, the University of Oregon’s Network Startup Resource Center (NSRC) and MIT’s Computer…
A team of researchers at Georgia State University has been awarded a prestigious five-year, $5 million grant from the National Science Foundation’s Centers of Research Excellence in Science and Technology (CREST) program, which…
The social, economic, and health impacts of the COVID-19 pandemic have disproportionately affected underserved populations in the United States, including racially minoritized students, lower-income students, and females. These populations have also been…

The University of Arkansas at Little Rock has received a $750,000 grant from the National Centers of Academic Excellence in Cybersecurity, located within the National Security Agency, and will be one of…
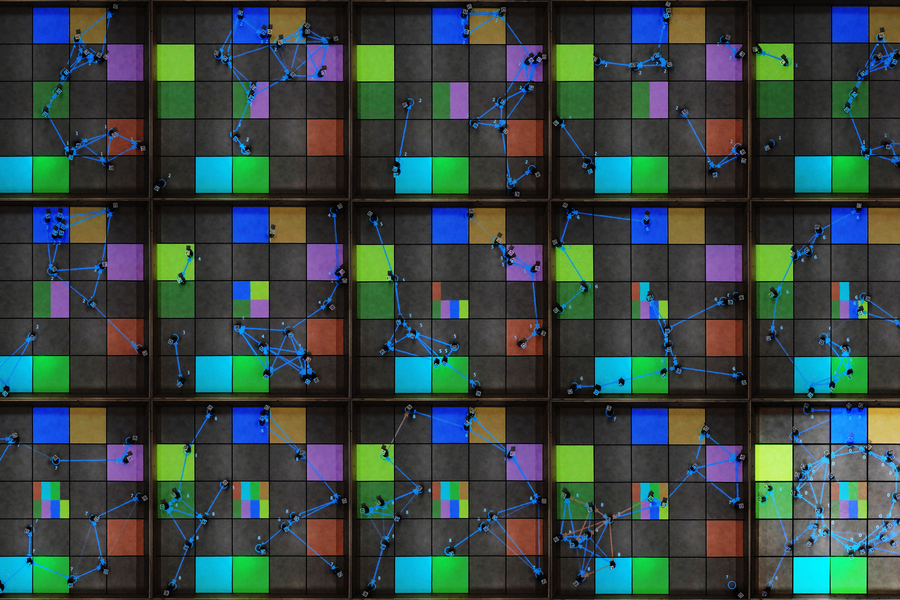
Imagine a team of autonomous drones equipped with advanced sensing equipment, searching for smoke as they fly high above the Sierra Nevada mountains. Once they spot a wildfire, these leader robots relay…

Vulnerabilities in Apple Pay and Visa could enable hackers to bypass an iPhone’s Apple Pay lock screen and perform contactless payments, according to research by the University of Birmingham and University…

Georgia Tech Researchers have now shown that one of the very measures meant to keep data secure on a low-end phone can enable attackers to steal it. Their paper, presented on September…

Organizations working to meaningfully improve diversity and inclusion in STEM may be missing a crucial consideration, new research suggests. Rather than organizations solely focusing on hiring more women or increasing the visibility…