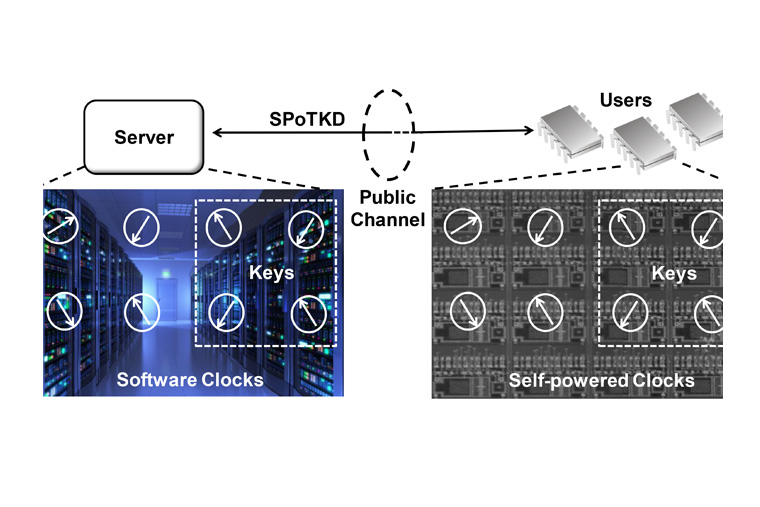
The NYU Tandon School of Engineering will showcase over 40 innovative and future-forward research projects by faculty and students, along with interactive, family-friendly tech activities, at its 2022 Research Excellence Exhibit. The annual expo, in…