At last week’s VMworld 2017, VMware announced the launch of AppDefense — a solution for securing applications running on virtualized or cloud environments. AppDefense — formerly known as “Goldilocks” — runs on vSphere,…
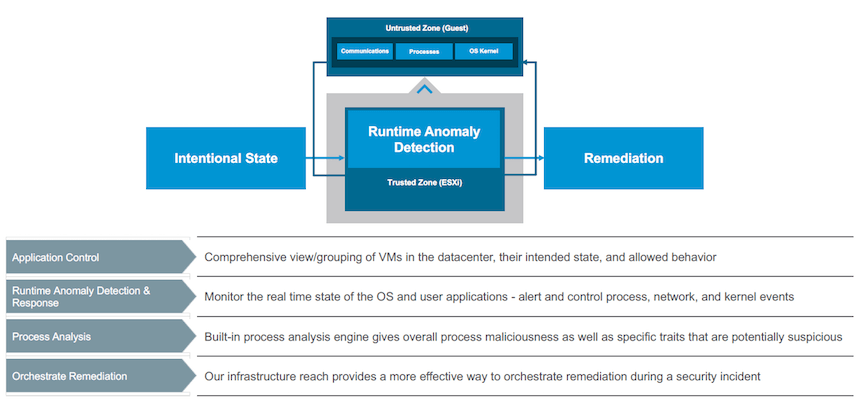

At last week’s VMworld 2017, VMware announced the launch of AppDefense — a solution for securing applications running on virtualized or cloud environments. AppDefense — formerly known as “Goldilocks” — runs on vSphere,…

For the first time, researchers have sent a quantum-secured message containing more than one bit of information per photon through the air above a city. The demonstration showed that it could one…
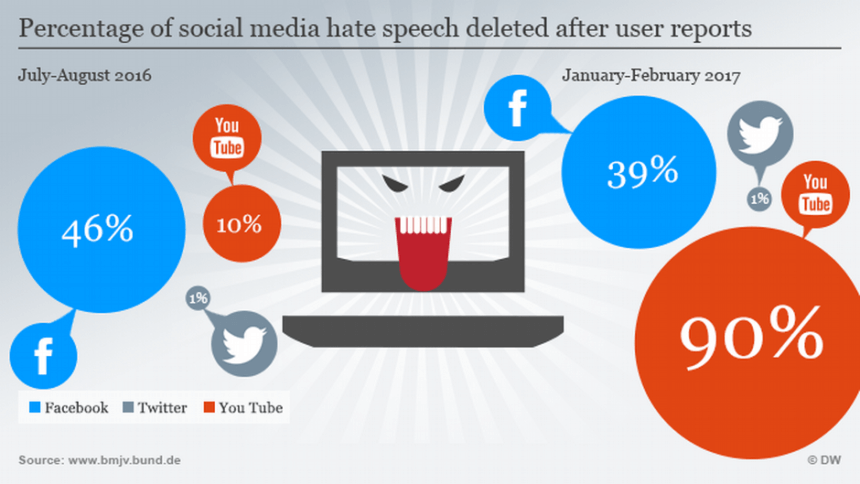
Extreme speech on social media—foul language, threats and overtly sexist and racist language—has been in the spotlight. While such language is not new, recent increases of extreme and offensive posts on social…

SecurityScorecard the other day released its annual U.S. State and Federal Government Cybersecurity Report. The study paints a grim picture of the overall cyber health of the U.S. government entities. In the midst of investigations into a…
How can humans best cooperate in an increasingly complex world? The Center for Peace and Security Studies (cPASS) at the University of California San Diego is working to find out by studying new and…

Beyond carrying all of our phone, text and internet communications, cyberspace is an active battleground, with cybercriminals, government agents and even military personnel probing weaknesses in corporate, national and even personal online…

Not all hackers are created equal. A hacker may typically be thought of as someone who infiltrates computer systems illegally for harmful purposes, and while this is certainly true of some hackers,…

USB connections, the most common interface used globally to connect external devices to computers, are vulnerable to information “leakage,” making them even less secure than has been thought, Australian research has shown.…

Understanding a cybercriminal’s backstory – where they live, what they do and who they know, is key to cracking cybercrime, new research suggests. Online crime is of course online, but there is also…